A randomized 25 question test from a pool of 761 questions, good luck!
A DDE protocol has 3 components to a "handle". Which of the components below would best be described as the name of a unique data source is contained inside of a DDE topic?
The data packet of an asychronous transmission contains _____ distinct types of bits. Choose the best answer to fill in the blank from the options below.
Each network layer for a DCS has it's own specialized equipment or software. Which of the layers below would make use of a DeviceNet protocol?
A typical HMI has several subsystems attached to it. Which of the subsystems below would be involved in the manipulation process control inputs?
Communication that is wireless in a SCADA system is common. Which of the communication methods below would be best defined as one that licensing would be required for most applications?
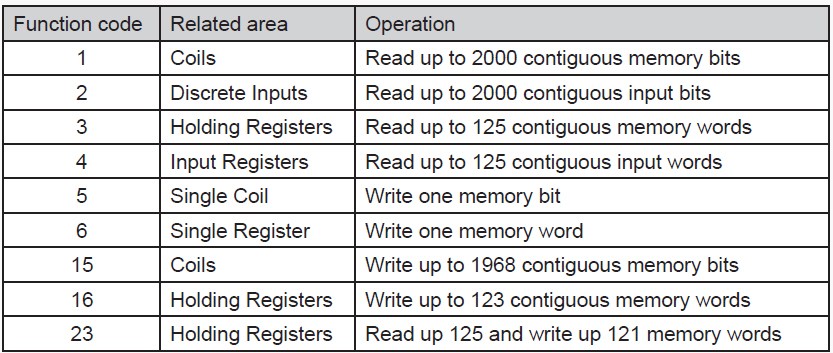
In the protocol specifications of Modbus, there are only four types of registers that can be accessed by the master. Which of the terms below is best described as a discreet input memory location?
Which of the components below is required for the H1 transmission segment to function?
Which of the signal transmission modes is best described as one that uses modulation to convert a received signal?
In IPv4, which of the protocols below has the additions of delivery acknowledgement and fragmentation/defragmentation?
There are several fields in an Ethernet message frame structure. Which of the answers represent the total amount of fields in an Ethernet message frame?
In IPv4, the user datagram protocol has less latency and measurable greater data throughput. Which of the answers below can be a drawback of this protocol?
In IPv4, if you are using a static IP address assignment, which of the actions from the answers below, are you preforming?
Data communication in a DCS takes the form of various net works. Which of the networks below would connect FCEs, field devices and sensors?
Which of the messaging types below is best described as direct communication with a field device initiated by the scanner module?
A typical DCS has at least four layers in it's architecture. Fieldbus and DeviceNet are all under the direct control of which of the layers below?
The wired Ethernet transmission standards are defined by the OSI model layers. Which of the answers below is one of those defining layers?
A defined area of geographical coverage is commonly called an area network. Which of the area networks below is used for schools, small localized businesses, and shopping malls?
In Modbus, data is read, and written in various memory ranges. Which of the answers below best represents the data type that a holding registers would use?
Providing power to remote sites in a SCADA system has several difficulties associated with it. Which of the answers below would be best defined as one that is used for continuous power generation where there are no other options?
Which of the answers below best represents the required nominal impedance of the data pair cabling in the DeviceNet system?
The leased lines in a SCADA system provides a communication link between locations that is a dedicated one. Which of the environments below would the leased lines reside?
There are several devices that reside at each layer within the a typical DCS. Which of the levels below is where PLC and SIS controllers reside?
Over the lifetime of a HMI, there will be changes to it's software form the supplier. Which of the terms below would best describe the red number in the picture below?

There are many options to choose from for alarm states. Which of the following alarm states can be best described as a temporary suppression of an alarm?
Which of the topology connections is the most typical for a HART communication device?